Netboot.xyz

Get Started with Apps!
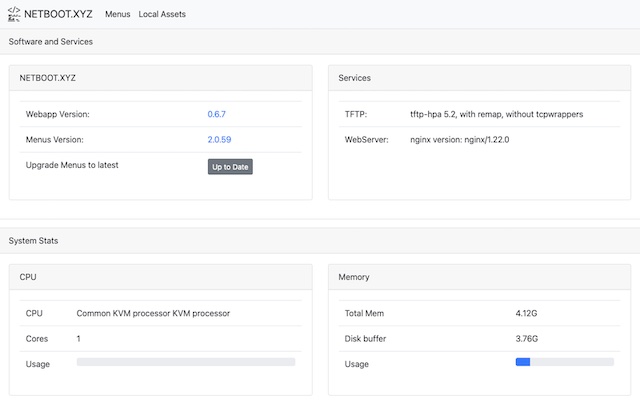
App Version: 0.7.6-nbxyz4 (Changelog)
Keywords: tftp, network, pxe, netboot, netbootxyz, netboot.xyz
Train: Community
Home Page: https://netboot.xyz
Added: 2024-08-02
Last Updated: 2026-01-27
netboot.xyz lets you PXE boot various operating system installers or utilities from a single tool over the network.
Run as Context- Container [netboot] runs as root user and group.
Group: 0 / Host group is [root]
User: 0 / Host user is [root]
Security Capabilities
- Netboot is able to change file ownership arbitrarily
- Netboot is able to bypass file permission checks
- Netboot is able to bypass permission checks for file operations
- Netboot is able to send signals to any process
- Netboot is able to bind to privileged ports (< 1024)
- Netboot is able to change group ID of processes
- Netboot is able to change user ID of processes
- Netboot is able to use chroot() system call
App Metadata (Raw File)
{
"1.2.18": {
"healthy": true,
"supported": true,
"healthy_error": null,
"location": "/__w/apps/apps/trains/community/netbootxyz/1.2.18",
"last_update": "2026-01-27 13:13:23",
"required_features": [],
"human_version": "0.7.6-nbxyz4_1.2.18",
"version": "1.2.18",
"app_metadata": {
"annotations": {
"min_scale_version": "24.10.2.2"
},
"app_version": "0.7.6-nbxyz4",
"capabilities": [
{
"description": "Netboot is able to change file ownership arbitrarily",
"name": "CHOWN"
},
{
"description": "Netboot is able to bypass file permission checks",
"name": "DAC_OVERRIDE"
},
{
"description": "Netboot is able to bypass permission checks for file operations",
"name": "FOWNER"
},
{
"description": "Netboot is able to send signals to any process",
"name": "KILL"
},
{
"description": "Netboot is able to bind to privileged ports (< 1024)",
"name": "NET_BIND_SERVICE"
},
{
"description": "Netboot is able to change group ID of processes",
"name": "SETGID"
},
{
"description": "Netboot is able to change user ID of processes",
"name": "SETUID"
},
{
"description": "Netboot is able to use chroot() system call",
"name": "SYS_CHROOT"
}
],
"categories": [
"networking"
],
"changelog_url": "https://github.com/netbootxyz/docker-netbootxyz/tags",
"date_added": "2024-08-02",
"description": "netboot.xyz lets you PXE boot various operating system installers or utilities from a single tool over the network.",
"home": "https://netboot.xyz",
"host_mounts": [],
"icon": "https://media.sys.truenas.net/apps/netbootxyz/icons/icon.png",
"keywords": [
"tftp",
"network",
"pxe",
"netboot",
"netbootxyz",
"netboot.xyz"
],
"lib_version": "2.1.77",
"lib_version_hash": "1837f8e69ae1adc313330c3b1c2615e9b4d03c5459d657a5898bae78090f8195",
"maintainers": [
{
"email": "dev@truenas.com",
"name": "truenas",
"url": "https://www.truenas.com/"
}
],
"name": "netbootxyz",
"run_as_context": [
{
"description": "Container [netboot] runs as root user and group.",
"gid": 0,
"group_name": "Host group is [root]",
"uid": 0,
"user_name": "Host user is [root]"
}
],
"screenshots": [
"https://media.sys.truenas.net/apps/netbootxyz/screenshots/screenshot1.jpg"
],
"sources": [
"https://github.com/netbootxyz/docker-netbootxyz",
"https://netboot.xyz"
],
"title": "Netboot.xyz",
"train": "community",
"version": "1.2.18"
},
"schema": {
"groups": [
{
"name": "Netboot.xyz Configuration",
"description": "Configure Netboot.xyz"
},
{
"name": "User and Group Configuration",
"description": "Configure User and Group for Netboot.xyz"
},
{
"name": "Network Configuration",
"description": "Configure Network for Netboot.xyz"
},
{
"name": "Storage Configuration",
"description": "Configure Storage for Netboot.xyz"
},
{
"name": "Labels Configuration",
"description": "Configure Labels for Netboot.xyz"
},
{
"name": "Resources Configuration",
"description": "Configure Resources for Netboot.xyz"
}
],
"questions": [
{
"variable": "TZ",
"group": "Netboot.xyz Configuration",
"label": "Timezone",
"schema": {
"type": "string",
"default": "Etc/UTC",
"required": true,
"$ref": [
"definitions/timezone"
]
}
},
{
"variable": "netbootxyz",
"label": "",
"group": "Netboot.xyz Configuration",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "tftpd_opts",
"label": "TFTPD Options",
"description": "Additional options for the TFTPD service.",
"schema": {
"type": "list",
"default": [],
"items": [
{
"variable": "opt",
"label": "Option",
"schema": {
"type": "string",
"required": true
}
}
]
}
},
{
"variable": "additional_envs",
"label": "Additional Environment Variables",
"schema": {
"type": "list",
"default": [],
"items": [
{
"variable": "env",
"label": "Environment Variable",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "name",
"label": "Name",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "value",
"label": "Value",
"schema": {
"type": "string"
}
}
]
}
}
]
}
}
]
}
},
{
"variable": "run_as",
"label": "",
"group": "User and Group Configuration",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "user",
"label": "User ID",
"description": "The user id that Netboot.xyz files will be owned by.",
"schema": {
"type": "int",
"min": 568,
"default": 568,
"required": true
}
},
{
"variable": "group",
"label": "Group ID",
"description": "The group id that Netboot.xyz files will be owned by.",
"schema": {
"type": "int",
"min": 568,
"default": 568,
"required": true
}
}
]
}
},
{
"variable": "network",
"label": "",
"group": "Network Configuration",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "tftp_port",
"label": "TFTP Port",
"description": "The TFTP port for netboot.xyz.",
"schema": {
"type": "dict",
"show_if": [
[
"host_network",
"=",
false
]
],
"attrs": [
{
"variable": "bind_mode",
"label": "Port Bind Mode",
"description": "The port bind mode.</br>\n- Publish: The port will be published on the host for external access.</br>\n- Expose: The port will be exposed for inter-container communication.</br>\n- None: The port will not be exposed or published.</br>\nNote: If the Dockerfile defines an EXPOSE directive,\nthe port will still be exposed for inter-container communication regardless of this setting.\n",
"schema": {
"type": "string",
"default": "published",
"enum": [
{
"value": "published",
"description": "Publish port on the host for external access"
},
{
"value": "exposed",
"description": "Expose port for inter-container communication"
},
{
"value": "",
"description": "None"
}
]
}
},
{
"variable": "port_number",
"label": "Port Number",
"schema": {
"type": "int",
"show_if": [
[
"bind_mode",
"=",
"published"
]
],
"default": 31009,
"min": 1,
"max": 65535,
"required": true
}
},
{
"variable": "host_ips",
"label": "Host IPs",
"description": "IPs on the host to bind this port",
"schema": {
"type": "list",
"show_if": [
[
"bind_mode",
"=",
"published"
]
],
"default": [],
"items": [
{
"variable": "host_ip",
"label": "Host IP",
"schema": {
"type": "string",
"required": true,
"$ref": [
"definitions/node_bind_ip"
]
}
}
]
}
}
]
}
},
{
"variable": "web_http_port",
"label": "Web HTTP Port",
"description": "The HTTP port for the netboot.xyz Portal.",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "bind_mode",
"label": "Port Bind Mode",
"description": "The port bind mode.</br>\n- Publish: The port will be published on the host for external access.</br>\n- Expose: The port will be exposed for inter-container communication.</br>\n- None: The port will not be exposed or published.</br>\nNote: If the Dockerfile defines an EXPOSE directive,\nthe port will still be exposed for inter-container communication regardless of this setting.\n",
"schema": {
"type": "string",
"default": "published",
"enum": [
{
"value": "published",
"description": "Publish port on the host for external access"
},
{
"value": "exposed",
"description": "Expose port for inter-container communication"
},
{
"value": "",
"description": "None"
}
]
}
},
{
"variable": "port_number",
"label": "Port Number",
"schema": {
"type": "int",
"default": 31010,
"min": 1,
"max": 65535,
"required": true
}
},
{
"variable": "host_ips",
"label": "Host IPs",
"description": "IPs on the host to bind this port",
"schema": {
"type": "list",
"show_if": [
[
"bind_mode",
"=",
"published"
]
],
"default": [],
"items": [
{
"variable": "host_ip",
"label": "Host IP",
"schema": {
"type": "string",
"required": true,
"$ref": [
"definitions/node_bind_ip"
]
}
}
]
}
}
]
}
},
{
"variable": "web_assets_port",
"label": "Web Assets Port",
"description": "The Assets port for the netboot.xyz, configures the NGINX_PORT variable on the container.",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "bind_mode",
"label": "Port Bind Mode",
"description": "The port bind mode.</br>\n- Publish: The port will be published on the host for external access.</br>\n- Expose: The port will be exposed for inter-container communication.</br>\n- None: The port will not be exposed or published.</br>\nNote: If the Dockerfile defines an EXPOSE directive,\nthe port will still be exposed for inter-container communication regardless of this setting.\n",
"schema": {
"type": "string",
"default": "published",
"enum": [
{
"value": "published",
"description": "Publish port on the host for external access"
},
{
"value": "exposed",
"description": "Expose port for inter-container communication"
},
{
"value": "",
"description": "None"
}
]
}
},
{
"variable": "port_number",
"label": "Port Number",
"schema": {
"type": "int",
"default": 31011,
"min": 1,
"max": 65535,
"required": true
}
},
{
"variable": "host_ips",
"label": "Host IPs",
"description": "IPs on the host to bind this port",
"schema": {
"type": "list",
"show_if": [
[
"bind_mode",
"=",
"published"
]
],
"default": [],
"items": [
{
"variable": "host_ip",
"label": "Host IP",
"schema": {
"type": "string",
"required": true,
"$ref": [
"definitions/node_bind_ip"
]
}
}
]
}
}
]
}
},
{
"variable": "host_network",
"label": "Host Network",
"description": "Bind to the host network. It's recommended to keep this disabled.\n",
"schema": {
"type": "boolean",
"default": true
}
}
]
}
},
{
"variable": "storage",
"label": "",
"group": "Storage Configuration",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "config",
"label": "Netboot.xyz Config Storage",
"description": "The path to store Netboot.xyz Config.",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "type",
"label": "Type",
"description": "ixVolume: Is dataset created automatically by the system.</br>\nHost Path: Is a path that already exists on the system.\n",
"schema": {
"type": "string",
"required": true,
"default": "ix_volume",
"enum": [
{
"value": "host_path",
"description": "Host Path (Path that already exists on the system)"
},
{
"value": "ix_volume",
"description": "ixVolume (Dataset created automatically by the system)"
}
]
}
},
{
"variable": "ix_volume_config",
"label": "ixVolume Configuration",
"description": "The configuration for the ixVolume dataset.",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"ix_volume"
]
],
"$ref": [
"normalize/ix_volume"
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "dataset_name",
"label": "Dataset Name",
"description": "The name of the dataset to use for storage.",
"schema": {
"type": "string",
"required": true,
"hidden": true,
"default": "config"
}
},
{
"variable": "acl_entries",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": []
}
}
]
}
},
{
"variable": "host_path_config",
"label": "Host Path Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"host_path"
]
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "acl",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": [],
"$ref": [
"normalize/acl"
]
}
},
{
"variable": "path",
"label": "Host Path",
"description": "The host path to use for storage.",
"schema": {
"type": "hostpath",
"show_if": [
[
"acl_enable",
"=",
false
]
],
"required": true
}
}
]
}
}
]
}
},
{
"variable": "assets",
"label": "Netboot.xyz Assets Storage",
"description": "The path to store Netboot.xyz Assets.",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "type",
"label": "Type",
"description": "ixVolume: Is dataset created automatically by the system.</br>\nHost Path: Is a path that already exists on the system.\n",
"schema": {
"type": "string",
"required": true,
"default": "ix_volume",
"enum": [
{
"value": "host_path",
"description": "Host Path (Path that already exists on the system)"
},
{
"value": "ix_volume",
"description": "ixVolume (Dataset created automatically by the system)"
}
]
}
},
{
"variable": "ix_volume_config",
"label": "ixVolume Configuration",
"description": "The configuration for the ixVolume dataset.",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"ix_volume"
]
],
"$ref": [
"normalize/ix_volume"
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "dataset_name",
"label": "Dataset Name",
"description": "The name of the dataset to use for storage.",
"schema": {
"type": "string",
"required": true,
"hidden": true,
"default": "assets"
}
},
{
"variable": "acl_entries",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": []
}
}
]
}
},
{
"variable": "host_path_config",
"label": "Host Path Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"host_path"
]
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "acl",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": [],
"$ref": [
"normalize/acl"
]
}
},
{
"variable": "path",
"label": "Host Path",
"description": "The host path to use for storage.",
"schema": {
"type": "hostpath",
"show_if": [
[
"acl_enable",
"=",
false
]
],
"required": true
}
}
]
}
}
]
}
},
{
"variable": "additional_storage",
"label": "Additional Storage",
"schema": {
"type": "list",
"default": [],
"items": [
{
"variable": "storageEntry",
"label": "Storage Entry",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "type",
"label": "Type",
"description": "ixVolume: Is dataset created automatically by the system.</br>\nHost Path: Is a path that already exists on the system.</br>\nSMB Share: Is a SMB share that is mounted to as a volume.</br>\nNFS Share: Is a NFS share that is mounted to as a volume.\n",
"schema": {
"type": "string",
"required": true,
"default": "ix_volume",
"enum": [
{
"value": "host_path",
"description": "Host Path (Path that already exists on the system)"
},
{
"value": "ix_volume",
"description": "ixVolume (Dataset created automatically by the system)"
},
{
"value": "cifs",
"description": "SMB/CIFS Share (Mounts a volume to a SMB share)"
},
{
"value": "nfs",
"description": "NFS Share (Mounts a volume to a NFS share)"
}
]
}
},
{
"variable": "read_only",
"label": "Read Only",
"description": "Mount the volume as read only.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "mount_path",
"label": "Mount Path",
"description": "The path inside the container to mount the storage.",
"schema": {
"type": "path",
"required": true
}
},
{
"variable": "host_path_config",
"label": "Host Path Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"host_path"
]
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "acl",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": [],
"$ref": [
"normalize/acl"
]
}
},
{
"variable": "path",
"label": "Host Path",
"description": "The host path to use for storage.",
"schema": {
"type": "hostpath",
"show_if": [
[
"acl_enable",
"=",
false
]
],
"required": true
}
}
]
}
},
{
"variable": "ix_volume_config",
"label": "ixVolume Configuration",
"description": "The configuration for the ixVolume dataset.",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"ix_volume"
]
],
"$ref": [
"normalize/ix_volume"
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "dataset_name",
"label": "Dataset Name",
"description": "The name of the dataset to use for storage.",
"schema": {
"type": "string",
"required": true,
"default": "storage_entry"
}
},
{
"variable": "acl_entries",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": []
}
}
]
}
},
{
"variable": "cifs_config",
"label": "SMB Configuration",
"description": "The configuration for the SMB dataset.",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"cifs"
]
],
"attrs": [
{
"variable": "server",
"label": "Server",
"description": "The server to mount the SMB share.",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "path",
"label": "Path",
"description": "The path to mount the SMB share.",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "username",
"label": "Username",
"description": "The username to use for the SMB share.",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "password",
"label": "Password",
"description": "The password to use for the SMB share.",
"schema": {
"type": "string",
"required": true,
"private": true
}
},
{
"variable": "domain",
"label": "Domain",
"description": "The domain to use for the SMB share.",
"schema": {
"type": "string"
}
}
]
}
},
{
"variable": "nfs_config",
"label": "NFS Configuration",
"description": "The configuration for the NFS dataset.",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"nfs"
]
],
"attrs": [
{
"variable": "server",
"label": "Server",
"description": "The server to mount the NFS share.",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "path",
"label": "Path",
"description": "The path to mount the NFS share.",
"schema": {
"type": "string",
"required": true
}
}
]
}
}
]
}
}
]
}
}
]
}
},
{
"variable": "labels",
"label": "",
"group": "Labels Configuration",
"schema": {
"type": "list",
"default": [],
"items": [
{
"variable": "label",
"label": "Label",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "key",
"label": "Key",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "value",
"label": "Value",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "containers",
"label": "Containers",
"description": "Containers where the label should be applied",
"schema": {
"type": "list",
"items": [
{
"variable": "container",
"label": "Container",
"schema": {
"type": "string",
"required": true,
"enum": [
{
"value": "netboot",
"description": "netboot"
}
]
}
}
]
}
}
]
}
}
]
}
},
{
"variable": "resources",
"label": "",
"group": "Resources Configuration",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "limits",
"label": "Limits",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "cpus",
"label": "CPUs",
"description": "CPUs limit for Netboot.xyz.",
"schema": {
"type": "int",
"default": 2,
"required": true
}
},
{
"variable": "memory",
"label": "Memory (in MB)",
"description": "Memory limit for Netboot.xyz.",
"schema": {
"type": "int",
"default": 4096,
"required": true
}
}
]
}
}
]
}
}
]
},
"readme": "<h1>Netboot.xyz</h1> <p><a href=\"https://netboot.xyz\">netboot.xyz</a> lets you PXE boot various operating system installers or utilities from a single tool over the network.</p>",
"changelog": null,
"chart_metadata": {
"annotations": {
"min_scale_version": "24.10.2.2"
},
"app_version": "0.7.6-nbxyz4",
"capabilities": [
{
"description": "Netboot is able to change file ownership arbitrarily",
"name": "CHOWN"
},
{
"description": "Netboot is able to bypass file permission checks",
"name": "DAC_OVERRIDE"
},
{
"description": "Netboot is able to bypass permission checks for file operations",
"name": "FOWNER"
},
{
"description": "Netboot is able to send signals to any process",
"name": "KILL"
},
{
"description": "Netboot is able to bind to privileged ports (< 1024)",
"name": "NET_BIND_SERVICE"
},
{
"description": "Netboot is able to change group ID of processes",
"name": "SETGID"
},
{
"description": "Netboot is able to change user ID of processes",
"name": "SETUID"
},
{
"description": "Netboot is able to use chroot() system call",
"name": "SYS_CHROOT"
}
],
"categories": [
"networking"
],
"changelog_url": "https://github.com/netbootxyz/docker-netbootxyz/tags",
"date_added": "2024-08-02",
"description": "netboot.xyz lets you PXE boot various operating system installers or utilities from a single tool over the network.",
"home": "https://netboot.xyz",
"host_mounts": [],
"icon": "https://media.sys.truenas.net/apps/netbootxyz/icons/icon.png",
"keywords": [
"tftp",
"network",
"pxe",
"netboot",
"netbootxyz",
"netboot.xyz"
],
"lib_version": "2.1.77",
"lib_version_hash": "1837f8e69ae1adc313330c3b1c2615e9b4d03c5459d657a5898bae78090f8195",
"maintainers": [
{
"email": "dev@truenas.com",
"name": "truenas",
"url": "https://www.truenas.com/"
}
],
"name": "netbootxyz",
"run_as_context": [
{
"description": "Container [netboot] runs as root user and group.",
"gid": 0,
"group_name": "Host group is [root]",
"uid": 0,
"user_name": "Host user is [root]"
}
],
"screenshots": [
"https://media.sys.truenas.net/apps/netbootxyz/screenshots/screenshot1.jpg"
],
"sources": [
"https://github.com/netbootxyz/docker-netbootxyz",
"https://netboot.xyz"
],
"title": "Netboot.xyz",
"train": "community",
"version": "1.2.18"
}
}
}Support, maintenance, and documentation for applications within the Community catalog is handled by the TrueNAS community. The TrueNAS Applications Market hosts but does not validate or maintain any linked resources associated with this app.
There currently aren’t any resources available for this application!
Please help the TrueNAS community add resources here or discuss this application in the TrueNAS Community forum.




