Vaultwarden

Vaultwarden
Get Started with Apps!
Get Started with Apps!
Requires TrueNAS: 24.10.2.2 or newer
App Version: 1.35.3 (Changelog)
Keywords: password, manager
Train: Community
Home Page: https://github.com/dani-garcia/vaultwarden
App Version: 1.35.3 (Changelog)
Keywords: password, manager
Train: Community
Home Page: https://github.com/dani-garcia/vaultwarden
Vaultwarden Details
Added: 2024-09-19
Last Updated: 2026-02-13
Added: 2024-09-19
Last Updated: 2026-02-13
Alternative implementation of the Bitwarden server API written in Rust and compatible with upstream Bitwarden clients.
Run as Context- Container [postgres] runs as non-root user and group.
Group: 999 / Host group is [docker]
User: 999 / Host user is [netdata] - Container [vaultwarden] can run as any non-root user and group.
Group: 568 / Host group is [apps]
User: 568 / Host user is [apps]
Screenshots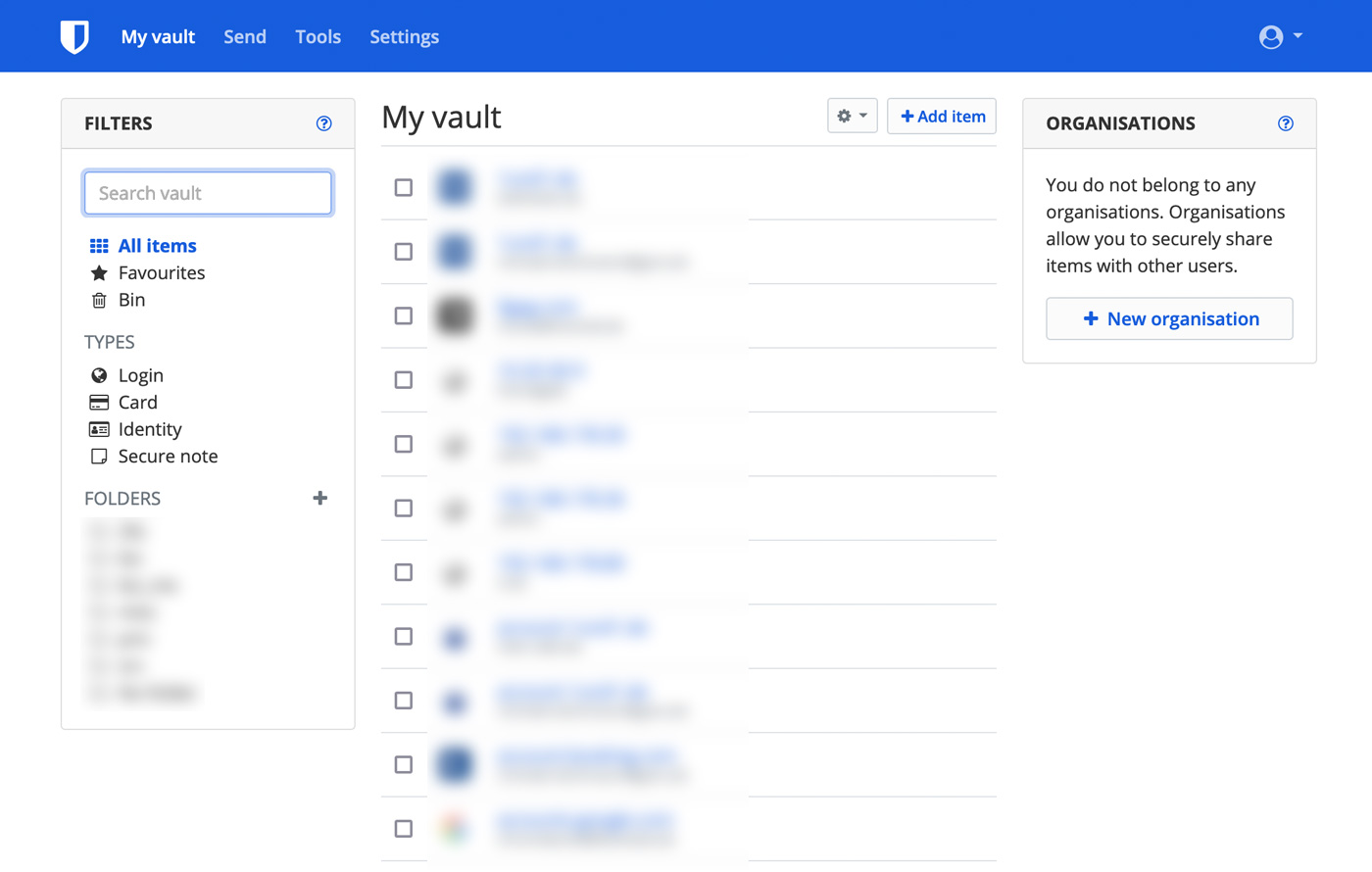

×
![Full Screenshot]()
App Metadata (Raw File)
{
"1.3.36": {
"healthy": true,
"supported": true,
"healthy_error": null,
"location": "/__w/apps/apps/trains/community/vaultwarden/1.3.36",
"last_update": "2026-02-13 14:33:03",
"required_features": [],
"human_version": "1.35.3_1.3.36",
"version": "1.3.36",
"app_metadata": {
"annotations": {
"min_scale_version": "24.10.2.2"
},
"app_version": "1.35.3",
"capabilities": [],
"categories": [
"security"
],
"changelog_url": "https://github.com/dani-garcia/vaultwarden/releases",
"date_added": "2024-09-19",
"description": "Alternative implementation of the Bitwarden server API written in Rust and compatible with upstream Bitwarden clients.",
"home": "https://github.com/dani-garcia/vaultwarden",
"host_mounts": [],
"icon": "https://media.sys.truenas.net/apps/vaultwarden/icons/icon.svg",
"keywords": [
"password",
"manager"
],
"lib_version": "2.1.77",
"lib_version_hash": "1837f8e69ae1adc313330c3b1c2615e9b4d03c5459d657a5898bae78090f8195",
"maintainers": [
{
"email": "dev@truenas.com",
"name": "truenas",
"url": "https://www.truenas.com/"
}
],
"name": "vaultwarden",
"run_as_context": [
{
"description": "Container [postgres] runs as non-root user and group.",
"gid": 999,
"group_name": "Host group is [docker]",
"uid": 999,
"user_name": "Host user is [netdata]"
},
{
"description": "Container [vaultwarden] can run as any non-root user and group.",
"gid": 568,
"group_name": "Host group is [apps]",
"uid": 568,
"user_name": "Host user is [apps]"
}
],
"screenshots": [
"https://media.sys.truenas.net/apps/vaultwarden/screenshots/screenshot1.png"
],
"sources": [
"https://github.com/dani-garcia/vaultwarden"
],
"title": "Vaultwarden",
"train": "community",
"version": "1.3.36"
},
"schema": {
"groups": [
{
"name": "Vaultwarden Configuration",
"description": "Configure Vaultwarden"
},
{
"name": "User and Group Configuration",
"description": "Configure User and Group for Vaultwarden"
},
{
"name": "Network Configuration",
"description": "Configure Network for Vaultwarden"
},
{
"name": "Storage Configuration",
"description": "Configure Storage for Vaultwarden"
},
{
"name": "Labels Configuration",
"description": "Configure Labels for Vaultwarden"
},
{
"name": "Resources Configuration",
"description": "Configure Resources for Vaultwarden"
}
],
"questions": [
{
"variable": "TZ",
"group": "Vaultwarden Configuration",
"label": "Timezone",
"schema": {
"type": "string",
"default": "Etc/UTC",
"required": true,
"$ref": [
"definitions/timezone"
]
}
},
{
"variable": "vaultwarden",
"label": "",
"group": "Vaultwarden Configuration",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "postgres_image_selector",
"label": "Postgres Image (CAUTION)",
"description": "If you are changing this after the postgres directory has been initialized,</br>\nSTOP! and make sure you have a backup of your data.</br>\nChanging this will trigger an one way database upgrade.</br>\nYou can only select newer versions of postgres.</br>\nSelecting an older version will refuse to start.</br>\nIf something goes wrong, you will have to restore from backup.\n",
"schema": {
"type": "string",
"default": "postgres_18_image",
"required": true,
"enum": [
{
"value": "postgres_15_image",
"description": "Postgres 15 (Deprecated)"
},
{
"value": "postgres_17_image",
"description": "Postgres 17"
},
{
"value": "postgres_18_image",
"description": "Postgres 18"
}
]
}
},
{
"variable": "db_password",
"label": "Database Password",
"description": "The password for Vaultwarden.",
"schema": {
"type": "string",
"default": "",
"required": true,
"private": true
}
},
{
"variable": "admin_token",
"label": "Admin Token",
"description": "Setting this, will enable the admin portal",
"schema": {
"type": "string",
"default": "",
"private": true
}
},
{
"variable": "enable_websocket",
"label": "Enable Websocket",
"description": "Enable Websocket for Vaultwarden.",
"schema": {
"type": "boolean",
"default": true
}
},
{
"variable": "additional_envs",
"label": "Additional Environment Variables",
"schema": {
"type": "list",
"default": [],
"items": [
{
"variable": "env",
"label": "Environment Variable",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "name",
"label": "Name",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "value",
"label": "Value",
"schema": {
"type": "string"
}
}
]
}
}
]
}
}
]
}
},
{
"variable": "run_as",
"label": "",
"group": "User and Group Configuration",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "user",
"label": "User ID",
"description": "The user id that Vaultwarden files will be owned by.",
"schema": {
"type": "int",
"min": 568,
"default": 568,
"required": true
}
},
{
"variable": "group",
"label": "Group ID",
"description": "The group id that Vaultwarden files will be owned by.",
"schema": {
"type": "int",
"min": 568,
"default": 568,
"required": true
}
}
]
}
},
{
"variable": "network",
"label": "",
"group": "Network Configuration",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "web_port",
"label": "WebUI Port",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "bind_mode",
"label": "Port Bind Mode",
"description": "The port bind mode.</br>\n- Publish: The port will be published on the host for external access.</br>\n- Expose: The port will be exposed for inter-container communication.</br>\n- None: The port will not be exposed or published.</br>\nNote: If the Dockerfile defines an EXPOSE directive,\nthe port will still be exposed for inter-container communication regardless of this setting.\n",
"schema": {
"type": "string",
"default": "published",
"enum": [
{
"value": "published",
"description": "Publish port on the host for external access"
},
{
"value": "exposed",
"description": "Expose port for inter-container communication"
},
{
"value": "",
"description": "None"
}
]
}
},
{
"variable": "port_number",
"label": "Port Number",
"schema": {
"type": "int",
"default": 30032,
"min": 1,
"max": 65535,
"required": true
}
},
{
"variable": "host_ips",
"label": "Host IPs",
"description": "IPs on the host to bind this port",
"schema": {
"type": "list",
"show_if": [
[
"bind_mode",
"=",
"published"
]
],
"default": [],
"items": [
{
"variable": "host_ip",
"label": "Host IP",
"schema": {
"type": "string",
"required": true,
"$ref": [
"definitions/node_bind_ip"
]
}
}
]
}
}
]
}
},
{
"variable": "certificate_id",
"label": "Certificate ID",
"description": "The certificate to use for Vaultwarden </br>\nUsing the Rocket method for TLS setup is NOT recommended </br>\nPrefer a reverse proxy with a valid certificate\n",
"schema": {
"type": "int",
"null": true,
"$ref": [
"definitions/certificate"
]
}
},
{
"variable": "domain",
"label": "Domain",
"description": "The domain to use for Vaultwarden </br>\nFormat is: https://sub.domain.tld:port\n",
"schema": {
"type": "uri",
"default": ""
}
}
]
}
},
{
"variable": "storage",
"label": "",
"group": "Storage Configuration",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "data",
"label": "Vaultwarden Data Storage",
"description": "The path to store Vaultwarden Data.",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "type",
"label": "Type",
"description": "ixVolume: Is dataset created automatically by the system.</br>\nHost Path: Is a path that already exists on the system.\n",
"schema": {
"type": "string",
"required": true,
"default": "ix_volume",
"enum": [
{
"value": "host_path",
"description": "Host Path (Path that already exists on the system)"
},
{
"value": "ix_volume",
"description": "ixVolume (Dataset created automatically by the system)"
}
]
}
},
{
"variable": "ix_volume_config",
"label": "ixVolume Configuration",
"description": "The configuration for the ixVolume dataset.",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"ix_volume"
]
],
"$ref": [
"normalize/ix_volume"
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "dataset_name",
"label": "Dataset Name",
"description": "The name of the dataset to use for storage.",
"schema": {
"type": "string",
"required": true,
"hidden": true,
"default": "data"
}
},
{
"variable": "acl_entries",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": []
}
}
]
}
},
{
"variable": "host_path_config",
"label": "Host Path Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"host_path"
]
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "acl",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": [],
"$ref": [
"normalize/acl"
]
}
},
{
"variable": "path",
"label": "Host Path",
"description": "The host path to use for storage.",
"schema": {
"type": "hostpath",
"show_if": [
[
"acl_enable",
"=",
false
]
],
"required": true
}
}
]
}
}
]
}
},
{
"variable": "postgres_data",
"label": "Vaultwarden Postgres Data Storage",
"description": "The path to store Vaultwarden Postgres Data.",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "type",
"label": "Type",
"description": "ixVolume: Is dataset created automatically by the system.</br>\nHost Path: Is a path that already exists on the system.\n",
"schema": {
"type": "string",
"required": true,
"default": "ix_volume",
"enum": [
{
"value": "host_path",
"description": "Host Path (Path that already exists on the system)"
},
{
"value": "ix_volume",
"description": "ixVolume (Dataset created automatically by the system)"
}
]
}
},
{
"variable": "ix_volume_config",
"label": "ixVolume Configuration",
"description": "The configuration for the ixVolume dataset.",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"ix_volume"
]
],
"$ref": [
"normalize/ix_volume"
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "dataset_name",
"label": "Dataset Name",
"description": "The name of the dataset to use for storage.",
"schema": {
"type": "string",
"required": true,
"hidden": true,
"default": "postgres_data"
}
},
{
"variable": "acl_entries",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": []
}
}
]
}
},
{
"variable": "host_path_config",
"label": "Host Path Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"host_path"
]
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "acl",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": [],
"$ref": [
"normalize/acl"
]
}
},
{
"variable": "path",
"label": "Host Path",
"description": "The host path to use for storage.",
"schema": {
"type": "hostpath",
"show_if": [
[
"acl_enable",
"=",
false
]
],
"required": true
}
},
{
"variable": "auto_permissions",
"label": "Automatic Permissions",
"description": "Automatically set permissions for the host path.\nEnabling this, will check the top level directory,</br>\nIf it finds incorrect permissions, it will `chown` the\nhost path to the user and group required for the\npostgres container.\n",
"schema": {
"type": "boolean",
"default": false,
"show_if": [
[
"acl_enable",
"=",
false
]
]
}
}
]
}
}
]
}
},
{
"variable": "additional_storage",
"label": "Additional Storage",
"schema": {
"type": "list",
"default": [],
"items": [
{
"variable": "storageEntry",
"label": "Storage Entry",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "type",
"label": "Type",
"description": "ixVolume: Is dataset created automatically by the system.</br>\nHost Path: Is a path that already exists on the system.</br>\nSMB Share: Is a SMB share that is mounted to as a volume.</br>\nNFS Share: Is a NFS share that is mounted to as a volume.\n",
"schema": {
"type": "string",
"required": true,
"default": "ix_volume",
"enum": [
{
"value": "host_path",
"description": "Host Path (Path that already exists on the system)"
},
{
"value": "ix_volume",
"description": "ixVolume (Dataset created automatically by the system)"
},
{
"value": "cifs",
"description": "SMB/CIFS Share (Mounts a volume to a SMB share)"
},
{
"value": "nfs",
"description": "NFS Share (Mounts a volume to a NFS share)"
}
]
}
},
{
"variable": "read_only",
"label": "Read Only",
"description": "Mount the volume as read only.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "mount_path",
"label": "Mount Path",
"description": "The path inside the container to mount the storage.",
"schema": {
"type": "path",
"required": true
}
},
{
"variable": "host_path_config",
"label": "Host Path Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"host_path"
]
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "acl",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": [],
"$ref": [
"normalize/acl"
]
}
},
{
"variable": "path",
"label": "Host Path",
"description": "The host path to use for storage.",
"schema": {
"type": "hostpath",
"show_if": [
[
"acl_enable",
"=",
false
]
],
"required": true
}
}
]
}
},
{
"variable": "ix_volume_config",
"label": "ixVolume Configuration",
"description": "The configuration for the ixVolume dataset.",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"ix_volume"
]
],
"$ref": [
"normalize/ix_volume"
],
"attrs": [
{
"variable": "acl_enable",
"label": "Enable ACL",
"description": "Enable ACL for the storage.",
"schema": {
"type": "boolean",
"default": false
}
},
{
"variable": "dataset_name",
"label": "Dataset Name",
"description": "The name of the dataset to use for storage.",
"schema": {
"type": "string",
"required": true,
"default": "storage_entry"
}
},
{
"variable": "acl_entries",
"label": "ACL Configuration",
"schema": {
"type": "dict",
"show_if": [
[
"acl_enable",
"=",
true
]
],
"attrs": [],
"$ref": [
"normalize/acl"
]
}
}
]
}
},
{
"variable": "cifs_config",
"label": "SMB Configuration",
"description": "The configuration for the SMB dataset.",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"cifs"
]
],
"attrs": [
{
"variable": "server",
"label": "Server",
"description": "The server to mount the SMB share.",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "path",
"label": "Path",
"description": "The path to mount the SMB share.",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "username",
"label": "Username",
"description": "The username to use for the SMB share.",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "password",
"label": "Password",
"description": "The password to use for the SMB share.",
"schema": {
"type": "string",
"required": true,
"private": true
}
},
{
"variable": "domain",
"label": "Domain",
"description": "The domain to use for the SMB share.",
"schema": {
"type": "string"
}
}
]
}
},
{
"variable": "nfs_config",
"label": "NFS Configuration",
"description": "The configuration for the NFS dataset.",
"schema": {
"type": "dict",
"show_if": [
[
"type",
"=",
"nfs"
]
],
"attrs": [
{
"variable": "server",
"label": "Server",
"description": "The server to mount the NFS share.",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "path",
"label": "Path",
"description": "The path to mount the NFS share.",
"schema": {
"type": "string",
"required": true
}
}
]
}
}
]
}
}
]
}
}
]
}
},
{
"variable": "labels",
"label": "",
"group": "Labels Configuration",
"schema": {
"type": "list",
"default": [],
"items": [
{
"variable": "label",
"label": "Label",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "key",
"label": "Key",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "value",
"label": "Value",
"schema": {
"type": "string",
"required": true
}
},
{
"variable": "containers",
"label": "Containers",
"description": "Containers where the label should be applied",
"schema": {
"type": "list",
"items": [
{
"variable": "container",
"label": "Container",
"schema": {
"type": "string",
"required": true,
"enum": [
{
"value": "vaultwarden",
"description": "vaultwarden"
},
{
"value": "postgres",
"description": "postgres"
}
]
}
}
]
}
}
]
}
}
]
}
},
{
"variable": "resources",
"label": "",
"group": "Resources Configuration",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "limits",
"label": "Limits",
"schema": {
"type": "dict",
"attrs": [
{
"variable": "cpus",
"label": "CPUs",
"description": "CPUs limit for Vaultwarden.",
"schema": {
"type": "int",
"default": 2,
"required": true
}
},
{
"variable": "memory",
"label": "Memory (in MB)",
"description": "Memory limit for Vaultwarden.",
"schema": {
"type": "int",
"default": 4096,
"required": true
}
}
]
}
}
]
}
}
]
},
"readme": "<h1>Vaultwarden</h1> <p><a href=\"https://github.com/dani-garcia/vaultwarden\">Vaultwarden</a> Alternative implementation of the <code>Bitwarden</code> server API written in Rust and compatible with upstream Bitwarden clients</p> <p>While the option to use <code>Rocket</code> for TLS is there, it is not <a href=\"https://github.com/dani-garcia/vaultwarden/wiki/Enabling-HTTPS#via-rocket\">recommended</a>. Instead, use a reverse proxy to handle TLS termination.</p> <p>Using <code>HTTPS</code> is <strong>required</strong> for the most of the features to work (correctly).</p>",
"changelog": null,
"chart_metadata": {
"annotations": {
"min_scale_version": "24.10.2.2"
},
"app_version": "1.35.3",
"capabilities": [],
"categories": [
"security"
],
"changelog_url": "https://github.com/dani-garcia/vaultwarden/releases",
"date_added": "2024-09-19",
"description": "Alternative implementation of the Bitwarden server API written in Rust and compatible with upstream Bitwarden clients.",
"home": "https://github.com/dani-garcia/vaultwarden",
"host_mounts": [],
"icon": "https://media.sys.truenas.net/apps/vaultwarden/icons/icon.svg",
"keywords": [
"password",
"manager"
],
"lib_version": "2.1.77",
"lib_version_hash": "1837f8e69ae1adc313330c3b1c2615e9b4d03c5459d657a5898bae78090f8195",
"maintainers": [
{
"email": "dev@truenas.com",
"name": "truenas",
"url": "https://www.truenas.com/"
}
],
"name": "vaultwarden",
"run_as_context": [
{
"description": "Container [postgres] runs as non-root user and group.",
"gid": 999,
"group_name": "Host group is [docker]",
"uid": 999,
"user_name": "Host user is [netdata]"
},
{
"description": "Container [vaultwarden] can run as any non-root user and group.",
"gid": 568,
"group_name": "Host group is [apps]",
"uid": 568,
"user_name": "Host user is [apps]"
}
],
"screenshots": [
"https://media.sys.truenas.net/apps/vaultwarden/screenshots/screenshot1.png"
],
"sources": [
"https://github.com/dani-garcia/vaultwarden"
],
"title": "Vaultwarden",
"train": "community",
"version": "1.3.36"
}
}
}Support, maintenance, and documentation for applications within the Community catalog is handled by the TrueNAS community. The TrueNAS Applications Market hosts but does not validate or maintain any linked resources associated with this app.




